So you’ve deployed your new VPS or cloud server and SSH is served up on port 22 with password authentication. If you’re reading this, you already know that’s entirely insecure and just begging to be attacked. I’ll detail my procedure for hardening SSH on Fedora Linux, the distro I run. This should also work on downstream RHEL and CentOS, and broadly speaking on any SSH server, though some bits may differ.
Two Ways to Fully Disable WordPress XML-RPC
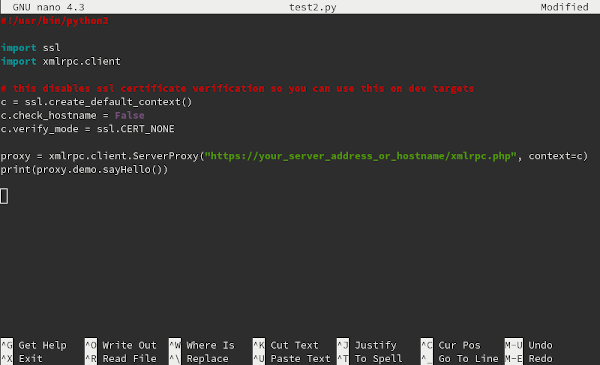
Back several years ago when XML-RPC attacks on WordPress were prevalent, I shared some techniques here for selectively countering such attacks. Most users, however, just want to shut XML-RPC off completely. They often land on the widely installed Disable XML-RPC plugin. This plugin unfortunately does not fully work. Let me show you why, share some better solutions, and update my unit testing code for Python 3 in the process.
Nmap Top Ports Frequencies Study
By default, Nmap scans the most common 1,000 TCP ports. How does it decide which ones, what coverage does that result in, and what are the ramifications for real world port scanning? Let’s look at the actual numbers behind Nmap’s top ports.
Querying the Pwned Passwords API to Identify Breached Passwords
Troy at haveibeenpwned.com has released an updated API for confidentially searching an enormous collection of breached login credentials, half a billion entries. Critically, the design of the API avoids transmitting any actual password value or even hashes.
Don’t Melt Down Over the Meltdown and Spectre Flaws
Quick take based on reading of others’ work, but unless you’re a datacenter operator, there is really no need to go into full bore panic and scrap your plans in the wake of the new disclosure of hardwired flaws in Intel and other CPUs.
Download MVPS HOSTS File Converted to Unix EOLs
Periodically I’ll be doing an ad-hoc deploy of MVPS HOSTS file on a Mac or Android system, and have to improvise a means to accomplish the required conversion from DOS to Unix line termination from the shell prompt.
Leaving Windows for Linux on my Primary System
Few outside the technology business may be fully aware that Windows 10 arrives in the context of a major strategy shift at Microsoft. Feeling the heat from Google, Apple, and others, Microsoft needs to mutate and evolve its business models to compete in the end user computing marketplace. Selling Windows and Office licenses for whatever number of cents OEMs pay them for the right to ship these products on newly purchased machines is no longer cutting it in an age of falling PC sales. There’s new business out there, a pie they’re hungry for a big piece of.
One More Check In on WordPress XML-RPC Fail2ban Traps
Just putting out an updated chart showing how this has performed through several additional months of operation. I’ve previously covered what’s happening here in detail when I began to sustain a high volume of attacks, when I implemented the fail2ban based countermeasures, and when I checked in on how the traps were performing four months ago.
How To Deploy MVPS HOSTS File on an Android Phone
I have replaced the default HOSTS file on my Android device with the MVPS HOSTS file, a blacklist for blocking advertising, tracking and malware-distributing server names. Installing this blacklist confers the same browsing security, privacy, and performance benefits on my phone as I have long enjoyed on conventional workstations: ad blocking, faster web page loads and decreased bandwidth usage, mitigation of browsing behavior profiling and contextual ad targeting, and reduced exposure to malware infection by malicious web sites. Allow me to demonstrate the specific procedure that I used and hopefully save others some time.